The authentication mechanism is very useful when we try to access a protected web resource; at that time the web container activates the authentication mechanism that has been configured for that resource. A web client can authenticate a user to a web server using one of the following mechanisms:
- HTTP Basic Authentication
- HTTP Digest Authentication
- Form Based Authentication
- HTTPS Client Authentication
HTTP Basic Authentication:
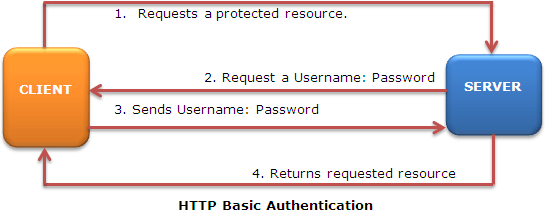
HTTP basic authentication is defined by the HTTP specification that lightly sends the user's user name and password over the Internet as text that is uu-encoded (Unix-to-Unix encoded) but not encrypted. If someone can intercept the transmission, the user name and password information can easily be decoded. It should only be used with HTTPS, as the password can be easily captured and reused over HTTP. Basic authentication is supported by Exchange 2000 Server and Exchange Server 2003.
With basic authentication, the following things occur:
- A client requests access to a protected resource.
- The web server returns a dialog box that requests the user name and password.
- The client submits the user name and password to the server.
- The server validates the credentials and, if successful, returns the requested resource.
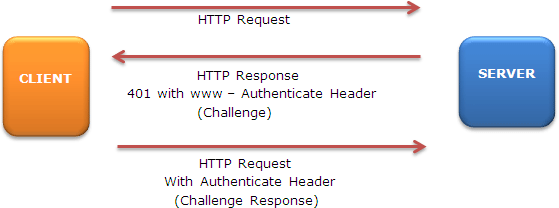
HTTP Digest Authentication:
Similar to HTTP Basic Authentication, HTTP Digest Authentication authenticates a user based on a username and a password. As Digest Authentication is not currently in widespread use, servlet containers are encouraged but NOT REQUIRED to support it. The advantage of this method is that the clear text password is protected in transmission; it cannot be determined from the digest that is submitted by the client to the server. Digested password authentication supports the concept of digesting user passwords. This causes the stored version of the passwords to be encoded in a form that is not easily reversible, but that the web server can still utilize for authentication.
The difference between basic and digest authentication is that on the network connection between the browser and the server, the passwords are encrypted, even on a non-SSL connection. Digested password is authentication based on the concept of a hash or digest. In this stored version, the passwords are encoded in a form that is not easily reversible and this is used for authentication.
Form Based Authentication:
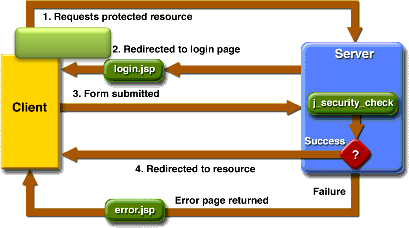
Particularly Form-based authentication is not secure. The content of the user dialog box is sent as plain text, and the target server is not authenticated. This form of authentication can expose the user names and passwords unless all connections are over SSL. If someone can intercept the transmission, the user name and password information can easily be decoded. However, we can use an Exchange2003 Server front-end with an Exchange2000 Server back-end and benefit from forms-based authentication. Forms-based authentication is supported only by Exchange Server 2003.
With form-based authentication, the following things occur:
- A client requests access to a protected resource.
- If the client is unauthenticated, the server redirects the client to a login page.
- The client submits the login form to the server.
- If the login succeeds, the server redirects the client to the resource. If the login fails, the client is redirected to an error page.
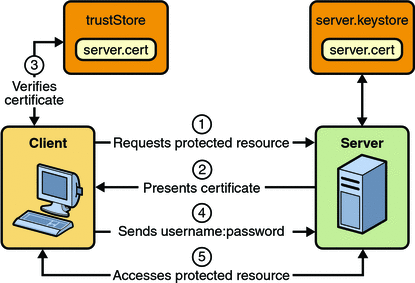
HTTPS Client Authentication:
Client-certificate authentication is a more secure method of authentication than BASIC or FORM authentication. It uses HTTP over SSL, in which the server and, optionally, the client authenticate one another using public key certificate. Secure Socket Layer (SSL) provides data encryption, server authentication, message integrity, and optional client authentication for a TCP/IP connection.