- Open the Central Administration site's web.config file
- Find the </configSections> entry
- Paste the following XML directly below it
- Find the <system.web> entry
- Paste the following XML directly below it
<roleManager enabled="true"
cacheRolesInCookie="false"
cookieName=".ASPXROLES"
cookieTimeout="30"
cookiePath="/"
cookieRequireSSL="false"
cookieSlidingExpiration="true"
cookieProtection="All"
defaultProvider="AspNetWindowsTokenRoleProvider"
createPersistentCookie="false"
maxCachedResults="25">
<providers>
<clear />
<add connectionStringName="AspNetSqlMembershipProvider"
applicationName="/"
name="SqlRole"
type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
<add applicationName="/"
name="AspNetWindowsTokenRoleProvider"
type="System.Web.Security.WindowsTokenRoleProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
</providers>
</roleManager>
<membership defaultProvider="SqlMember"
userIsOnlineTimeWindow="15" hashAlgorithmType="">
<providers>
<clear />
<add connectionStringName="AspNetSqlMembershipProvider"
enablePasswordRetrieval="false"
enablePasswordReset="true"
requiresQuestionAndAnswer="true"
passwordAttemptWindow="10"
applicationName="/"
requiresUniqueEmail="false"
passwordFormat="Hashed"
name="SqlMember"
type="System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
</providers>
</membership>
- You have to check whether the <membership> and <rolemanager> entries only exist once. Delete any double entries.
- Paste the following XML below the <PeoplePickerWildcards> entry.
<clear />
<add key="AspNetSqlMembershipProvider" value="%" />
<add key="SqlMember" value="%"/>
<add key="SqlRole" value="%"/>
Adjust the web.config of the Security Token Service (STS) virtual directory
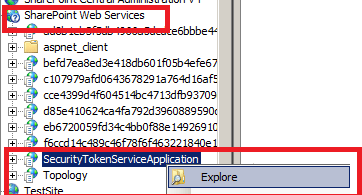
The SecurityTokenServiceApplication website is located under the SharePoint Web Services website, as shown in Figure. Go to your IIS and find the SecurityTokenServiceApplication and open it.
- Open the Security Token Service (STS) virtual directory's web.config file
- Find the </system.net> entry
- Paste the following XML directly below it
<connectionStrings>
<clear />
<add name="AspNetSqlMembershipProvider" connectionString="data source=Database name Security=SSPI;Initial Catalog=DB Name"
providerName="System.Data.SqlClient" />
</connectionStrings>
- Add a <system.web> entry directly below the </connectionStrings>
- Paste the following XML directly below the <system.web> entry
<roleManager enabled="true"
cacheRolesInCookie="false"
cookieName=".ASPXROLES"
cookieTimeout="30"
cookiePath="/"
cookieRequireSSL="false"
cookieSlidingExpiration="true"
cookieProtection="All"
defaultProvider="AspNetWindowsTokenRoleProvider"
createPersistentCookie="false"
maxCachedResults="25">
<providers>
<clear />
<add connectionStringName="AspNetSqlMembershipProvider"
applicationName="/"
name="SqlRole"
type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
<add applicationName="/"
name="AspNetWindowsTokenRoleProvider"
type="System.Web.Security.WindowsTokenRoleProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
</providers>
</roleManager>
<membership defaultProvider="SqlMember"
userIsOnlineTimeWindow="15" hashAlgorithmType="">
<providers>
<clear />
<add connectionStringName="AspNetSqlMembershipProvider"
enablePasswordRetrieval="false"
enablePasswordReset="true"
requiresQuestionAndAnswer="true"
passwordAttemptWindow="10"
applicationName="/"
requiresUniqueEmail="false"
passwordFormat="Hashed"
name="SqlMember"
type="System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
</providers>
</membership>
- Add a </system.web> entry directly below it
Adjust the web.config of the claims based web application
- Open the claims based web application's web.config file
- Find the </configSections> entry
- Paste the following XML directly below it
<connectionStrings>
<clear />
<add name="AspNetSqlMembershipProvider"
connectionString="data source=Database name Security=SSPI;Initial Catalog=DB Name"
providerName="System.Data.SqlClient" /></connectionStrings>
- Locate the <membership> entry
- Replace everything from <membership> to </membership> with the following XML
<membership defaultProvider="i"
userIsOnlineTimeWindow="15"
hashAlgorithmType="">
<providers>
<clear />
<add connectionStringName="AspNetSqlMemberShipProvider"
enablePasswordRetrieval="false"
enablePasswordReset="true"
requiresQuestionAndAnswer="true"
passwordAttemptWindow="10"
applicationName="/"
requiresUniqueEmail="false"
passwordFormat="Hashed"
name="SqlMember"
type="System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
<add name="i"
type="Microsoft.SharePoint.Administration.Claims.SPClaimsAuthMembershipProvider,
Microsoft.SharePoint, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c" />
</providers>
</membership>
- Locate the <roleManager> entry
- Replace everything from <roleManager> to </roleManager> with the following XML:
<roleManager enabled="true"
cacheRolesInCookie="false"
cookieName=".ASPXROLES"
cookieTimeout="30"
cookiePath="/"
cookieRequireSSL="false"
cookieSlidingExpiration="true"
cookieProtection="All"
defaultProvider="c"
createPersistentCookie="false"
maxCachedResults="25">
<providers>
<clear />
<add connectionStringName="AspNetSqlMemberShipProvider"
applicationName="/"
name="AspNetSqlRoleProvider"
type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
<add applicationName="/"
name="SqlRole"
type="System.Web.Security.WindowsTokenRoleProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
<add name="c" type="Microsoft.SharePoint.Administration.Claims.SPClaimsAuthRoleProvider,
Microsoft.SharePoint, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c" />
</providers>
</roleManager>
- Locate the <roleManager> entry
- Replace everything from <roleManager> to </roleManager> with the following XML:
<roleManager enabled="true"
cacheRolesInCookie="false"
cookieName=".ASPXROLES"
cookieTimeout="30"
cookiePath="/"
cookieRequireSSL="false"
cookieSlidingExpiration="true"
cookieProtection="All"
defaultProvider="c"
createPersistentCookie="false"
maxCachedResults="25">
<providers>
<clear />
<add connectionStringName="AspNetSqlMemberShipProvider"
applicationName="/"
name="AspNetSqlRoleProvider"
type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
<add applicationName="/"
name="SqlRole"
type="System.Web.Security.WindowsTokenRoleProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
<add name="c" type="Microsoft.SharePoint.Administration.Claims.SPClaimsAuthRoleProvider,
Microsoft.SharePoint, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c" />
</providers>
</roleManager>
- Paste the following XML below the PeoplePickerWildcards entry
<clear />
<add key="AspNetSqlMembershipProvider" value="%" />
<add key="SqlMember" value="%"/>
<add key="SqlRole" value="%"/>